Cybersecurity should be one of your highest priorities.
2020 changed how people work and how businesses run. The move away from onsite servers and towards the cloud has accelerated with the need to adapt to a work-from-home environment.
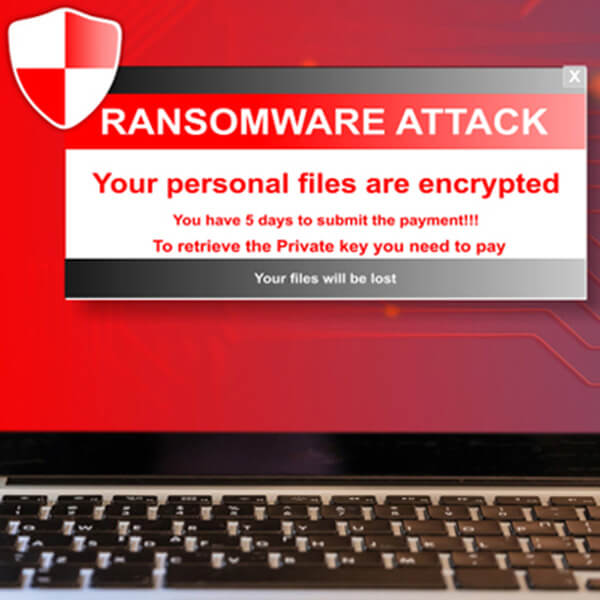
Technology is at the center of your organization. It manages all of your information, provides access to your staff to enhance their processes and is your connection to those you serve. As essential as technology has become to success, it also presents many risks. Cybersecurity should be one of your highest priorities.
Check out our IT Security Checklist below to help keep your business safe and prepared:
Documented Policies
Including technology-related policies and procedures in your employees’ company handbook will ensure that employees observe mandatory security measures. Documented policies list the security guidelines and obligations of employees when interacting with company systems or networks. Common policies to include are acceptable use, internet access, email and communication, remote access and encryption privacy.
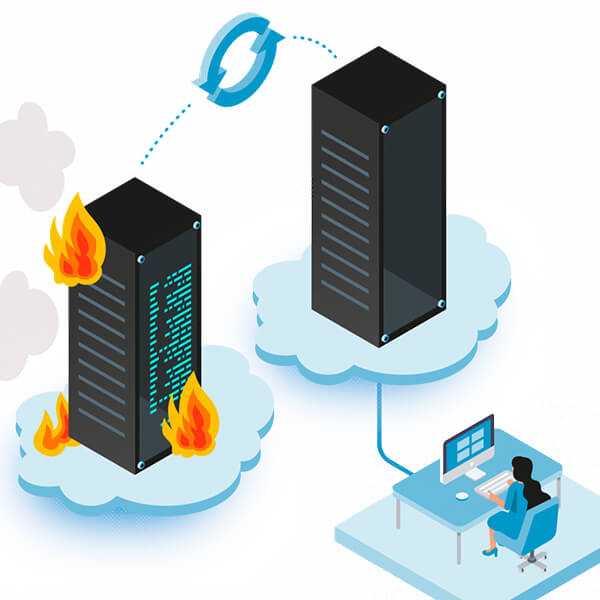
Disaster Recovery Policy
Businesses should maintain effective disaster recovery policies. A disaster recovery policy contains a set of actions that users should undertake to recover from an attack. Developing effective disaster recovery policies can facilitate a company’s efforts to contain an attack.
Updated Software
Utilizing up-to-date software is vital to enhancing the security of an organization. This is because modern software programs are developed to be resilient against current risks and attacks.
Employee Training
Cybersecurity ignorance can and will lead to cyberattacks. For example, an employee leaving a computer on without locking can result in data breaches. All organizations need to include training to provide employees with skills for securely using organizational systems, data and networks. This ensures that employees are capable of identifying security risks, managing them and reporting them to the relevant personnel.
Doceo can help!
Our team of seasoned IT Professionals can help you adapt to this rapid change, allowing you to focus on running your business and serving your clients.
Are you ready to discover how we can protect your company against digital threats?
Take a few minutes to fill out our Contact Form. An experienced IT Systems Specialist will be in touch with you.